Approaches to detect and prevent network traffic from malicious networks
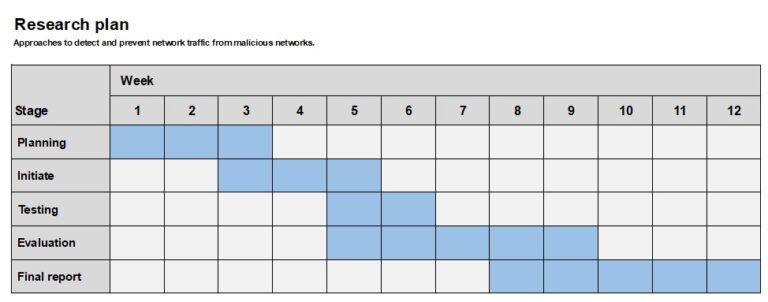
Research proposal AbstractConstantly, around the clock, reconnaissance is conducted for vulnerable systems and services around the world. This is done manually or automated by malicious actors and can be more or less systematic. To carry out these reconnaissance, tools are…
